//
Data Security and Privacy in A/R Automation: How Finance Leaders Protect Cash, Customers, and Compliance in 2025
A Comprehensive Analysis of Financial Operations, Regulatory Compliance, and Cyber Resilience in 2025
The Convergence of Finance and Cybersecurity
The line between financial operations and cybersecurity has effectively vanished. In 2025, accounts receivable is not only about invoices and aging reports, it is a high value target for attackers and a focal point for regulators.
The average cost of a data breach in the United States has climbed above 10 million dollars, with global averages still above 4 million dollars per incident, driven by detection, response, and legal costs documented in recent data breach studies. Those studies also show that organizations still need roughly eight months on average to identify and contain a breach, which means an attacker can dwell silently in finance systems for most of a year before being discovered.
Small and mid sized businesses are not exempt. Recent SMB cybersecurity research and surveys of smaller firms report that more than nine in ten SMBs faced at least one cyberattack in the last year and a majority fear that a serious breach could threaten their survival.
Invoices, payment instructions, and customer records sit at the center of this risk. Business email compromise, fake billing, and account takeover all flow through A/R. Moving from manual, email based invoicing to secure, automated A/R is no longer just an efficiency choice, it is a core risk management decision.
This article examines why manual A/R is inherently fragile, how modern compliance frameworks shape A/R design, what a secure automation architecture looks like, and how AI changes both the threat and the defense.
The High Stakes of Manual Financial Workflows
The Economic and Security Costs of Human Error
Manual invoicing and spreadsheet driven A/R carry structural weaknesses. Benchmarking from invoice automation research shows that manual processing often costs 15 to 16 dollars per invoice, while automated workflows can reduce that to roughly 3 dollars. That is an 80 percent cost reduction before you even consider security.
Manual data entry also introduces an error rate in the one to five percent range for many organizations. In a business issuing 1,000 invoices per month, that can mean dozens of incorrect invoices that need rework, often at a cost above 50 dollars per error when you factor in staff time, corrections, and follow up, as highlighted in analyses of hidden AR costs.
Those errors are not just operational noise. A mistyped email address or misrouted PDF can expose personally identifiable information or confidential pricing to unauthorized recipients, creating a reportable data breach under privacy regimes such as GDPR, CCPA, or PIPEDA.
The Velocity of Money and Operational Drag
Manual A/R also slows the velocity of cash. It can take ten to fifteen minutes to process a single invoice when staff key data, attach PDFs, and send emails. In many firms, that delay compounds into backlogs where teams report being weeks or even months behind on receivables and reconciliation, patterns documented in A/R statistics for 2024.
When reconciliation is slow, fraud is harder to spot. If no one reconciles bank activity against invoices for several weeks, subtle diversions of funds, duplicated payments, or unauthorized credits can sit unseen. Automated A/R that posts payments and reconciles in real time shortens that window and surfaces anomalies quickly.
Business Email Compromise: The Manual Workflow Killer
Business email compromise has become one of the most expensive forms of attack. Recent BEC statistics estimate average losses near 5 million dollars per incident, and a large share of organizations report facing BEC attempts that target finance and billing functions.
In manual workflows, invoices are sent as attachments from shared mailboxes and bank details appear directly in PDFs. Attackers who compromise or spoof those email addresses can quietly change account numbers or send fraudulent “updated bank details” messages. Customers follow the false instructions and funds disappear offshore.
Secure A/R platforms mitigate this by moving invoicing and payment into authenticated portals, where banking details are tokenized, stored with the payment processor, and never exposed in email. Customers log into a known domain, see locked in payment options, and pay within that environment, drastically reducing the attack surface.
Manual vs Automated A/R: Cost and Risk Profile
Metric | Manual AR Process | Automated AR Process | Impact |
Cost per invoice | 15 – 16 USD | ~3 USD | ~80 percent cost reduction |
Error rate | 1.6 – 5 percent | < 1 percent | Lower correction and leakage risk |
Correction cost | ~53 USD per error | Negligible | Significant operational savings |
Processing time | ~15 minutes | Seconds or minutes | Faster cash flow, lower backlog |
BEC vulnerability | High, email based | Low, portal based | Stronger protection against fraud |
Values adapted from invoice cost benchmarks, A/R efficiency analyses, and BEC loss data.
The Regulatory Landscape: PCI, HIPAA, SOC 2, and Data Residency
PCI DSS 4.0 and Payment Scope
Any business that processes, stores, or transmits card data must comply with PCI DSS. The shift to PCI DSS 4.0, with full enforcement in 2025, raises expectations for strong authentication, continuous risk management, and stricter control of the cardholder data environment, as summarized in recent PCI compliance guides and mid market primers.
For A/R, the practical insight is scope reduction. When your staff take card numbers over the phone or store them in local systems, your entire network can fall into PCI scope. When customers enter card data directly into a secure, PCI compliant processor via your A/R portal, the card number is converted into a token and your own environment never sees the raw PAN. This dramatically reduces both risk and audit burden, a strategy echoed in payment providers’ own PCI explanations.
HIPAA and Healthcare A/R
For clinics and healthcare providers, invoices often include protected health information. Billing therefore must satisfy HIPAA’s Security Rule and Privacy Rule, not just basic privacy laws. Recent studies of healthcare data security and HIPAA compliance challenges for small practices highlight the cost and complexity of managing PHI securely.
Manual billing through unencrypted email or generic SMS can easily violate HIPAA unless patients provide informed consent for such channels. By contrast, A/R platforms that provide encrypted portals, role based access, and immutable audit trails for every access or change to a patient account make it far easier to demonstrate compliance, as outlined in HIPAA billing and communication guidance and medical billing best practices.
SOC 2 and Vendor Assurance
SOC 2 has become the standard yardstick for SaaS vendors handling financial data. A SOC 2 Type II report confirms that a provider’s controls for security, availability, processing integrity, confidentiality, and privacy operate effectively over time, not just on paper.
When you select an A/R automation partner, you are effectively trusting them with your receivables infrastructure. Resources such as SOC 2 overviews and guides written for A/R automation buyers emphasize verifying current SOC 2 Type II status, not simply accepting a vendor’s verbal assurances.
Data Residency and Cross Border Considerations
For Canadian firms, data residency matters. PIPEDA and certain provincial laws require that personal information be stored and accessed under specific conditions. Public sector entities in provinces like British Columbia and Nova Scotia face stricter in country storage requirements, as outlined in analyses of Canadian data residency rules.
An A/R platform that offers regional data hosting options or clear guarantees around where data is stored and how it is replicated makes it easier to satisfy these expectations and align with CRA requirements for the retention of digital records.
The Architecture of Secure A/R Automation
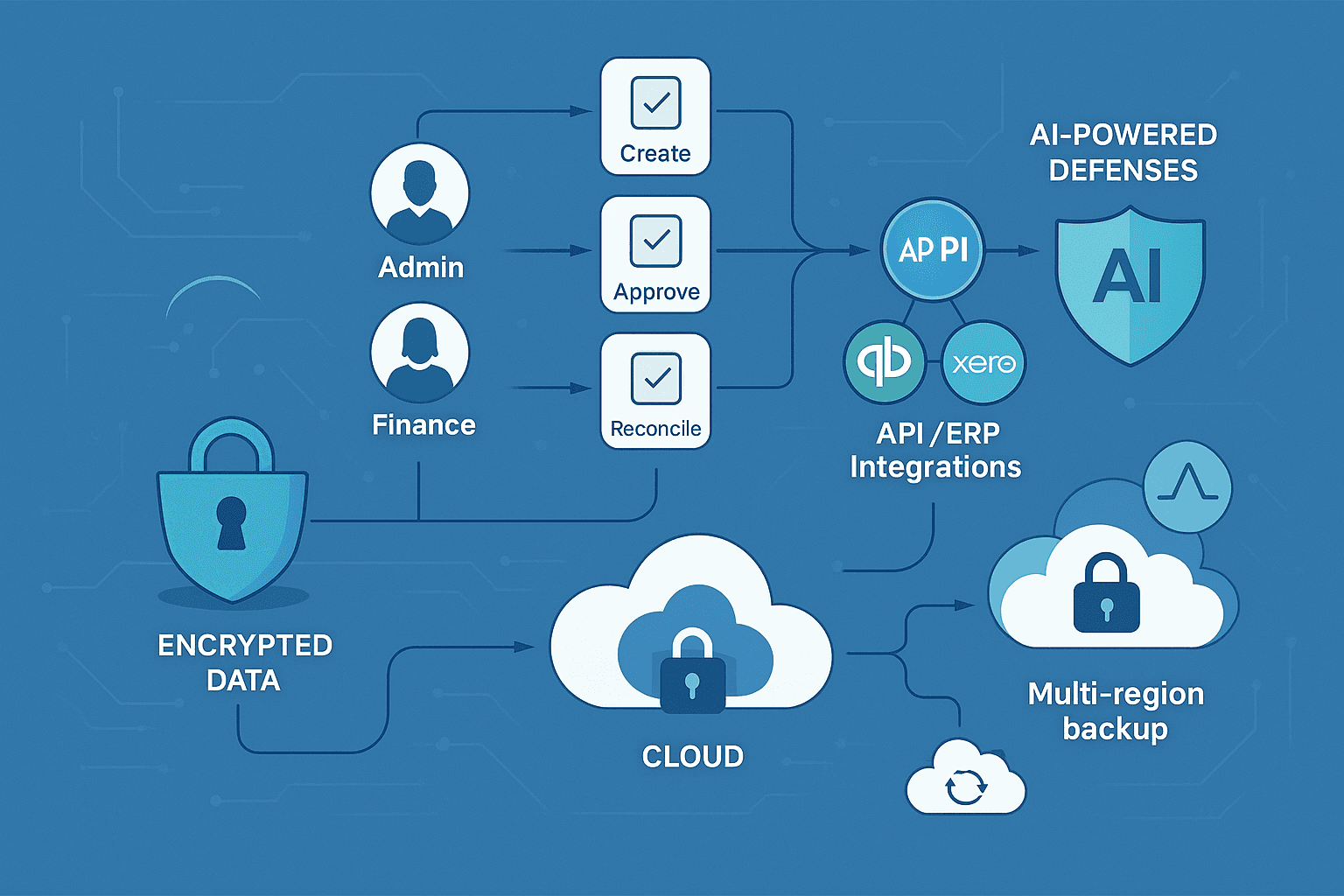
Encryption as Baseline
Secure A/R platforms treat financial and personal data with bank grade encryption. At rest, leading providers use AES 256, a standard described in detail in technical explainers on AES encryption and financial data protection. In transit, Transport Layer Security (TLS) protects sessions between browsers, APIs, and servers, the same approach used by major payment services that advertise bank level protection.
Role Based Access and Segregation of Duties
Strong platforms embed role based access control so that users only see and change what their role requires. Overviews of RBAC and user access control in accounting highlight how limiting privileges reduces damage when a single account is compromised.
Segregation of duties is built into workflows. One user can create a customer, another can approve a credit memo, a third can reconcile bank statements. Guidance on SoD in receivables and university control practices shows how splitting responsibilities reduces the risk of insider fraud and accidental misstatements. In a modern A/R platform, these rules are enforced by the software, not just by policy documents.
API Security and ERP Integration
A/R automation depends on deep integrations with ERPs like NetSuite, QuickBooks, and Microsoft Dynamics. These connections must be secure. Best practice guidance for NetSuite integrations and developer security emphasizes OAuth 2.0, token revocation, rate limiting, and secure storage of API secrets in vaults rather than source code.
A secure A/R platform will inherit and extend these practices, so that data flows between systems without exposing credentials or opening the door to abuse.
AI in A/R: New Threats and New Defenses
AI Enabled Fraud
As AI capabilities expand, attackers use them to automate and personalize scams. Deepfake voice attacks, where an executive’s voice is cloned and used to request urgent transfers, have already appeared in consumer advisories and bank warnings about AI voice scams.
At the same time, AI agents and chatbots can be manipulated through prompt injection attacks that try to trick them into revealing sensitive information or performing unauthorized actions, risks outlined in prompt injection explainers and playbooks on deploying agentic AI safely.
AI as Guardian
On the defensive side, AI is becoming central to fraud detection. Models can learn normal payment patterns for each customer and flag anomalies, as explored in discussions of AI powered fraud prevention in A/R and AI in receivables.
Behavioral biometrics and device analytics are increasingly layered into authentication flows, and predictive risk scoring helps A/R teams identify customers likely to pay late before invoices even go past due, allowing earlier intervention and tighter terms.
For finance leaders, the key is choosing A/R platforms that not only use AI for efficiency but also embed AI driven security and anomaly detection.
A Security Checklist for A/R Leaders
When you evaluate A/R automation vendors, security has to be part of the business case, not a footnote. Practical checklists for cyber and fraud risk, such as small business security best practices and bank fraud prevention guides, can be adapted directly to A/R.
You should expect at minimum:
Current SOC 2 Type II attestation and, if processing payments, PCI DSS compliance at the appropriate level.
End to end encryption with AES 256 at rest and TLS 1.2 or higher in transit.
Strong access governance with SSO, MFA, RBAC, and revocation procedures.
Documented disaster recovery objectives and multi region redundancy.
Internally, you still need to maintain core hygiene: mandatory MFA on all finance systems, rigorous verification of any change to bank details, regular permission reviews based on least privilege, and recurring training to keep staff skeptical of urgent, authority based requests, as stressed in cyber audit guidance for accounting.
Where Abivo Fits in the Security Ecosystem
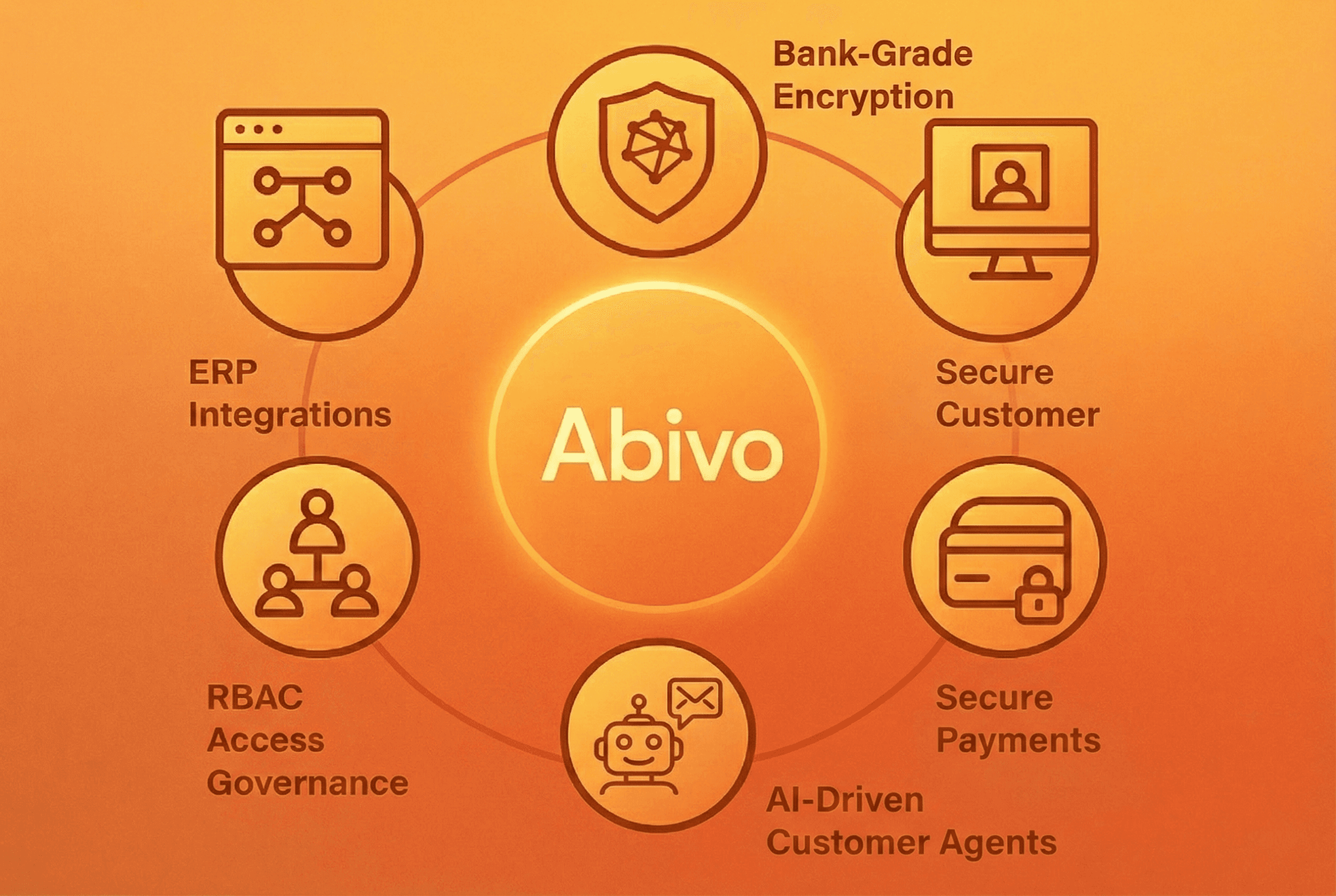
Abivo is built for service based SMBs that need both automation and assurance. By integrating with ERPs like QuickBooks, NetSuite, Xero, Sage, Microsoft Dynamics, FreshBooks, Stripe, Square Invoices, SAP Business One, Jobber, ServiceTitan, BuildOps, and Bill.com, Abivo sits at the center of your receivables stack.
From a security standpoint, Abivo’s design aligns with the principles outlined above:
Bank grade encryption for data in motion and at rest.
Role based access, audit trails, and segregation of duties inside the A/R workflow.
Secure payment flows that keep card data with the processor, not on your servers.
AI driven agents that call and email customers within controlled boundaries, reducing manual handling of sensitive data and cutting the risk of human error.
Instead of bolting security onto a manual A/R process, Abivo embeds it into the core of how invoices are issued, chased, and collected.
Secure Automation as the New Baseline
In 2025, manual A/R processes are not just slow and expensive, they are structurally misaligned with the realities of cyber risk and regulatory scrutiny. With breach costs rising, AI powered fraud emerging, and compliance frameworks tightening, finance leaders cannot afford to treat A/R automation as a nice to have.
Secure, compliant automation that encrypts data, limits access, removes payment details from email, and watches for anomalies in real time is becoming the baseline. For SMBs and mid market service businesses, this is how A/R shifts from a soft target to a hardened, resilient function that protects cash, customers, and reputation.
The safest invoice in this new environment is the one that flows from creation to payment without ever leaving a secure, automated system.

